This is the 39th article in the award-winning “Real Words or Buzzwords?” series about how real words become empty words and stifle technology progress.
By Ray Bernard, PSP, CHS-III
Though commonly misunderstood, the concept of fog computing has become critically important to physical security systems.
All-in-one RWOB
MAXIMIZE YOUR SECURITY OPERATIONS CAPABILITIES
Upgrade your security operations effectiveness through Security Technology Strategic Planning. Provably get more for your company's security technology investment.
★ ★ ★ GET NOTIFIED! ★ ★ ★
SIGN UP to be notified by email the day a new Real Words or Buzzwords? article is posted!
Real Words or Buzzwords?
The Award-Winning Article Series
#1 Proof of the buzzword that killed tech advances in the security industry—but not other industries.
#2 Next Generation (NextGen): A sure way to tell hype from reality.
#3 Customer Centric: Why all security industry companies aren't customer centric.
#4 Best of Breed: What it should mean to companies and their customers.
#5 Open: An openness scale to rate platforms and systems
#6 Network-friendly: It's much more than network connectivity.
#7 Mobile first: Not what it sounds like.
#8 Enterprise Class (Part One): To qualify as Enterprise Class system today is world's beyond what it was yesterday.
#9 Enterprise Class (Part Two): Enterprise Class must be more than just a top-level label.
#10 Enterprise Class (Part Three): Enterprise Class must be 21st century technology.
#11 Intuitive: It’s about time that we had a real-world testable definition for “intuitive”.
#12 State of the Art: A perspective for right-setting our own thinking about technologies.
#13 True Cloud (Part One): Fully evaluating cloud product offerings.
#14 True Cloud (Part Two): Examining the characteristics of 'native-cloud' applications.
#15 True Cloud (Part Three): Due diligence in testing cloud systems.
#16 IP-based, IP-enabled, IP-capable, or IP-connectable?: A perspective for right-setting our own thinking about technologies.
#17 Five Nines: Many people equate high availability with good user experience, yet many more factors are critically important.
#18 Robust: Words like “robust” must be followed by design specifics to be meaningful.
#19 Serverless Computing – Part 1: Why "serverless computing" is critical for some cloud offerings.
#20 Serverless Computing – Part 2: Why full virtualization is the future of cloud computing.
#21 Situational Awareness – Part 1: What products provide situational awareness?
#22 Situational Awareness – Part 2: Why system designs are incomplete without situational awareness?
#23 Situational Awareness – Part 3: How mobile devices change the situational awareness landscape?
#24 Situational Awareness – Part 4: Why situational awareness is a must for security system maintenance and acceptable uptime.
#25 Situational Awareness – Part 5: We are now entering the era of smart buildings and facilities. We must design integrated security systems that are much smarter than those we have designed in the past.
#26 Situational Awareness – Part 6: Developing modern day situational awareness solutions requires moving beyond 20th century thinking.
#27 Situational Awareness – Part 7: Modern day incident response deserves the help that modern technology can provide but doesn’t yet. Filling this void is one of the great security industry opportunities of our time.
#28 Unicity: Security solutions providers can spur innovation by envisioning how the Unicity concept can extend and strengthen physical access into real-time presence management.
#29 The API Economy: Why The API Economy will have a significant impact on the physical security industry moving forward.
#31 The Built Environment: In the 21st century, “the built environment” means so much more than it did just two decades ago.
#32 Hyper-Converged Infrastructure: Hyper-Converged Infrastructure has been a hot phrase in IT for several years, but do its promises hold true for the physical security industry?
#33 Software-Defined: Cloud-computing technology, with its many software-defined elements, is bringing self-scaling real-time performance capabilities to physical security system technology.
#34 High-Performance: How the right use of "high-performance" can accelerate the adoption of truly high-performing emerging technologies.
#35 Erasure Coding: Why RAID drive arrays don’t work anymore for video storage, and why Erasure Coding does.
#36 Presence Control: Anyone responsible for access control management or smart building experience must understand and apply presence control.
#37 Internet+: The Internet has evolved into much more than the information superhighway it was originally conceived to be.
#38 Digital Twin: Though few in physical security are familiar with the concept, it holds enormous potential for the industry.
#39 Fog Computing: Though commonly misunderstood, the concept of fog computing has become critically important to physical security systems.
#40 Scale - Part 1: Although many security-industry thought leaders have advocated that we should be “learning from IT,” there is still insufficient emphasis on learning about IT practices, especially for large-scale deployments.
#41 Scale - Part 2: Why the industry has yet to fully grasp what the ‘Internet of Things’ means for scaling physical security devices and systems.
#42 Cyberspace - Part 1: Thought to be an outdated term by some, understanding ‘Cyberspace’ and how it differs from ‘Cyber’ is paramount for security practitioners.
#43 Cyber-Physical Systems - Part 1: We must understand what it means that electronic physical security systems are cyber-physical systems.
#44 Cyberspace - Part 2: Thought to be an outdated term by some, understanding ‘Cyberspace’ and how it differs from ‘Cyber’ is paramount for security practitioners.
#45 Artificial Intelligence, Machine Learning and Deep Learning: Examining the differences in these technologies and their respective benefits for the security industry.
#46 VDI – Virtual Desktop Infrastructure: At first glance, VDI doesn’t seem to have much application to a SOC deployment. But a closer look reveals why it is actually of critical importance.
#47 Hybrid Cloud: The definition of hybrid cloud has evolved, and it’s important to understand the implications for physical security system deployments.
#48 Legacy: How you define ‘legacy technology’ may determine whether you get to update or replace critical systems.
#49 H.264 - Part 1: Examining the terms involved in camera stream configuration settings and why they are important.
#50 H.264 - Part 2: A look at the different H.264 video frame types and how they relate to intended uses of video.
#51 H.264 - Part 3: Once seen as just a marketing term, ‘smart codecs’ have revolutionized video compression.
#52 Presence Technologies: The proliferation of IoT sensors and devices, plus the current impacts of the COVID-19 pandemic, have elevated the capabilities and the importance of presence technologies.
#53 Anonymization, Encryption and Governance: The exponential advance of information technologies requires an exponential advance in the application of data protection.
#54 Computer Vision: Why a good understanding of the computer vision concept is important for evaluating today’s security video analytics products.
#55 Exponential Technology Advancement: The next 10 years of security technology will bring more change than in the entire history of the industry to now.
#56 IoT and IoT Native: The next 10 years of security technology will bring more change than in the entire history of the industry to now.
#57 Cloud Native IoT: A continuing look at what it means to have a 'True Cloud' solution and its impact on today’s physical security technologies.
#58 Bluetooth vs. Bluetooth LE: The next 10 years of security technology will bring more change than in the entire history of the industry to now.
#59 LPWAN - Low-Power Wide Area Networks: Emerging IoT smart sensor devices and systems are finding high-ROI uses for building security and safety.
#60 Edge Computing and the Evolving Internet: Almost 15 billion personal mobile devices and over 22 billion IoT devices operating daily worldwide have shifted the Internet’s “center of gravity” from its core to its edge – with many implications for enterprise physical security deployments
#61 Attack Surface: (Published as a Convergence Q&A Column article)An attack surface is defined as the total number of all possible entry points for unauthorized access into any system.
#62 Autonomous Compute Infrastructure: We’re on the brink of a radical new approach to technology, driven by autonomous operations.
#63 Physical Security Watershed Moment: We have reached a juncture in physical security technology that is making most of our past thinking irrelevant.
#64 Access Chaos: For 50 years we have had to live with physical access control systems that were not manageable at any large scale.
#65 AI and Automatiom: Will engineering talent, business savvy and capital investment from outside the physical security industry bring technology startups that transform reactive security to proactive and preventive security operations?
#66 Interoperability: Over the next five years, the single greatest determinant of the extent to which existing security industry companies will thrive or die is interoperability.
#67 AI Model : One key factor affects the accuracy, speed and computational requirements of AI
#68 Interoperability – Part 2: There are two types of security system interoperability – both of which are important considerations in the design of security systems and the selection of security system products.
#69 Interoperability – Part 3: There are two types of security system interoperability – both of which are important considerations in the design of security systems and the selection of security system products.
#70 Operationalizing AI: AI is not a product, but a broad category of software that enables products and systems to do more than ever before possible. How do we put it to good use?
#71 Shallow IT Adoption – Part 1: It’s not just about being IT compliant, it’s also about leveraging IT capabilities to properly serve the needs and wants of today’s technologically savvy customers.
#72 E-waste – an important security system design issue: Now e-waste is an important design issue not just because of growing e-waste regulations, but because educated designers can save enterprise security system customers a lot of money.
#73 LRPoE - Long Reach Power over Ethernet: A dozen factors have improved the business attractiveness of network cameras, making it more desirable to place cameras further from existing IT closets than the 328 foot limitation of standard Ethernet cable.
#74 NIST Declares Physical Access Control Systems are OT: Does it really mean anything that OT has joined the parade of labels (IT, IoT, and then IIoT) variously getting applied to security systems?
#75 Future Ready: Google sees the term "future-ready" trending up across many subject domains. But does that term apply to the physical security industry and its customers?
#76 Data KLiteracy: AI needs data. Thus, the ability of any department or division in an organization (including security) to use AI effectively depends on its ability to effectively obtain and utilize data – including security.
#77 Security Intelligence (upcoming): AI brings two kinds of intelligence to physical security systems – people bring the third.
More to come about every other week.
There is also a time factor involved, because technology trends reshape technologies (trends such as virtualization, miniaturization, low power, greater network capacity) and so technologies evolve for new applications, thus expanding or revising the original definitions of its terms. Thus today, authoritative online and print sources provide conflicting definitions for fog computing, edge computing and other terms.
As it so happens, the concepts of edge computing and fog computing have become critically important to electronic physical security systems. By not understanding them we face two dangers. First, it will be easy to dismiss fog computing by considering that “fog” is just more marketing hype about “edge” computing. Second, we’ll believe that we’ve been doing edge computing for over a decade with, for example, enterprise IP camera video surveillance systems – and thus think there is nothing really for us to learn.
When I first saw fog computing mentioned in an article online, I thought it was just another marketing hype term, and so I dismissed it. (I also made that mistake with Hyper-Converged Infrastructure.) A year later in 2015, I came across a very informative Cisco blog titled, “IoT, from Cloud to Fog Computing” by Maher Abdelshkour that provided detail on the Fog Computing concept.
The article said, “Cisco defines Fog Computing as a paradigm that extends Cloud computing and services to the edge of the network. Similar to Cloud, Fog provides data, compute, storage, and application services to end-users. The distinguishing Fog characteristics are its proximity to end-users, its dense geographical distribution, and its support for mobility.” This is true for online services like Amazon, Facebook or Google. But it’s not the right definition for physical security.
There was no mention in the Cisco article of physical security systems technology, even though the article described what we were already doing in the physical security industry with IP camera surveillance systems, so I dismissed it again as another fancy word for edge computing.”
Now, in retrospect, I can see that the Fog computing concept was still evolving (meaning that it was incomplete from today’s perspective) because the hardware and software technologies involved in it were rapidly evolving and changing what was possible to accomplish. Thus, it wasn’t evident yet that emerging-technology factors would make Fog Computing critically important to physical security system design and to the value that we could start delivering to end users in 2019. Silicon Valley area companies and some critical infrastructure organizations are now deploying such technology, and we’ll soon start seeing case studies and white papers detailing such deployments.
What Exactly is Fog Computing?
For several years I have referred to fog computing as “cloud on the ground” for two reasons. First, it makes a nice visual image with which its concepts can be easily associated. Second, fog computing uses cloud computing technologies in end-user premises deployments, including serverless computing and software-defined networks, storage and computing resources deployed as hyper-converged infrastructure (HCI). For many deployments these systems are cloud-connected and utilize cloud-computing for near-real-time applications – another reason to call it “cloud on the ground”.
Although the Wikipedia entry and many articles on fog computing equate it with edge computing, for industrial IoT systems (the technology category for electronic physical security systems) there is a distinction to be made between fog and edge computing.
See Figure 1 below, which is taken from the article titled, Cloud, Fog, Edge computing – What’s the Difference?, provided by WINSYSTEMS, INC., a company whose industrial controls products I’ve worked with since the mid-1990s, and whose WINSIGHTS blog is one of the most informative I’ve seen regarding industrial controls computing and networking.
Figure 1. Cloud, Fog and Edge Computing.
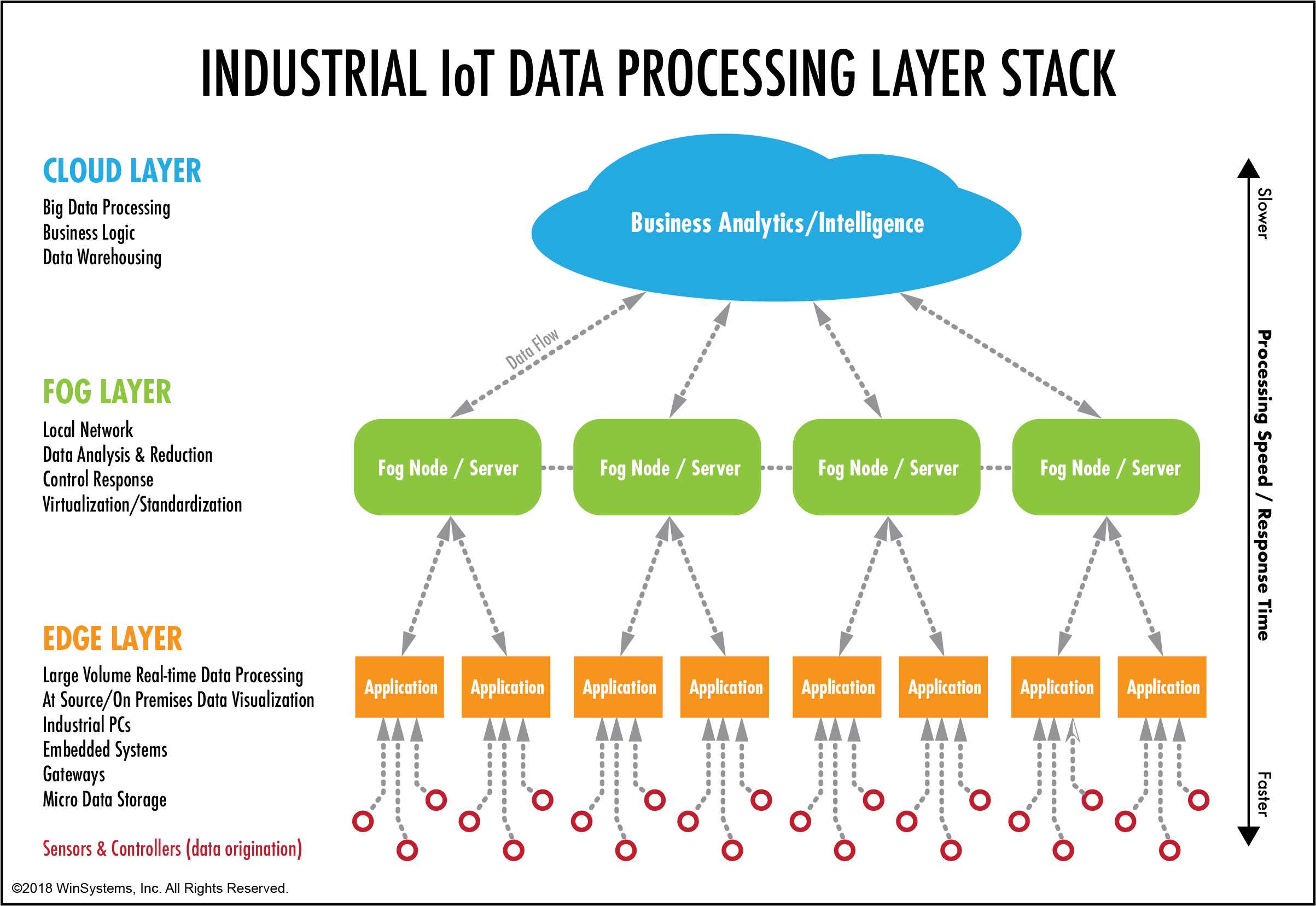
Image Source: WINSYSTEMS, Inc.
When you try to apply the cloud, fog and edge layers to security video systems – it’s not as simple as one might hope. It’s a little blurry because video processing and on-premises data visualization is performed both on-camera (obviously an edge device) and on a VMS system’s recording or video processing server (such as an AI/Analytics video processing server). Additionally, now and especially going forward, many video analytics functions will also be performed in the cloud as well as on the cameras and VMS servers.
For cyber-security planning purposes, it makes the most sense to consider cameras as being in the edge layer, VMS and related servers in the fog layer, and cloud-based services (of course) in the cloud layer. These three layers typically have different cybersecurity measures applied to them.
The first document to address this kind of edge-vs.-fog confusion – which is really more a problem of labelling than one of system design – is the NIST Special Publication 500-325 titled, “Fog Computing Conceptual Model”, which was published in March of 2018. Figure 2 below, from page 2 of the document, shows the NIST fog computing layered model, which does fit nicely with the Figure 1 diagram that was published a few months prior by WINSYSTEMS.
Figure 2. NIST Fog Computing Layered Model.
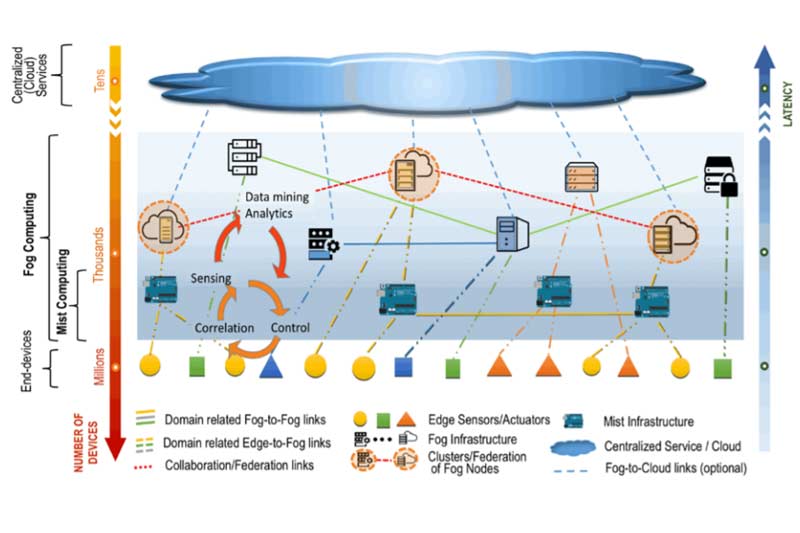
Image Source: NIST.
At the bottom of page two, the NIST document states, “Different usecase scenarios might have different architectures based on the optimal approach to supporting end-devices functionality. The choice of such representation is rooted in the intend of capturing a complex architecture that incorporates fog computing services.”
NIST also defines six Fog Computing Essential Characteristics, all of which apply to electronic physical security systems, and of which the “Real-time interactions” characteristic is becoming increasingly feasible and valuable given the many emerging AI deep learning capabilities that can be applied to video. At its recent partner conference, Milestone unveiled an R&D project that uses AI deep learning to configure video cameras in real time, optimizing their performance based on real-time lighting and other conditions to ensure that the camera is always performing optimally for its specific purpose. (See the demonstration video at https://youtu.be/uqYlxiyAHoA.)
NIST defines Fog Node as physical equipment (such as gateways, switches, routers, servers, etc.) or virtual components (such as virtualized switches and virtual machines) that are tightly coupled with the intelligent end devices and provide computing resources to the devices. The intelligent end devices are the controllers that interact with the cameras and card readers, for example. There are also five Fog Node Attributes, all of which should be part of the design thinking for most electronic physical security systems.
Mist Computing
Technically speaking, cameras could easily be considered a mist computing layer. I didn’t make this up. NIST describes it like this: “Mist computing uses microcomputers and microcontrollers to feed into fog computing nodes and potentially onward towards the centralized (cloud) computing services.” The thing to remember in reviewing the article by WINSYSTEMS and the NIST fog computing guidance, is that that labels exist so that we can have a commonly understood way of referring to the elements of the system designs being developed and deployed using current information technology elements. As we continue to apply emerging technology capabilities in our security products, systems and applications, the use of these labels will make more sense and have more value.
Advancing Security Technology
The system architectures and labels presented above were not designed for the legacy technology that now constitutes most of today’s deployed security technology. But they were designed for the technology that is already available from Intel, Dell, VMware, and others – technology on which companies are now building security products and systems.
Ray Bernard, PSP CHS-III, is the principal consultant for Ray Bernard Consulting Services (RBCS), a firm that provides security consulting services for public and private facilities (www.go-rbcs.com). In 2018 IFSEC Global listed Ray as #12 in the world’s Top 30 Security Thought Leaders. He is the author of the Elsevier book Security Technology Convergence Insights available on Amazon. Mr. Bernard is a Subject Matter Expert Faculty of the Security Executive Council (SEC) and an active member of the ASIS International member councils for Physical Security and IT Security. Follow Ray on Twitter: @RayBernardRBCS.
© 2019 RBCS

