This is the 59th article in the award-winning “Real Words or Buzzwords?” series about how real words become empty words and stifle technology progress, also published on SecurityInfoWatch.com.
By Ray Bernard, PSP, CHS-III
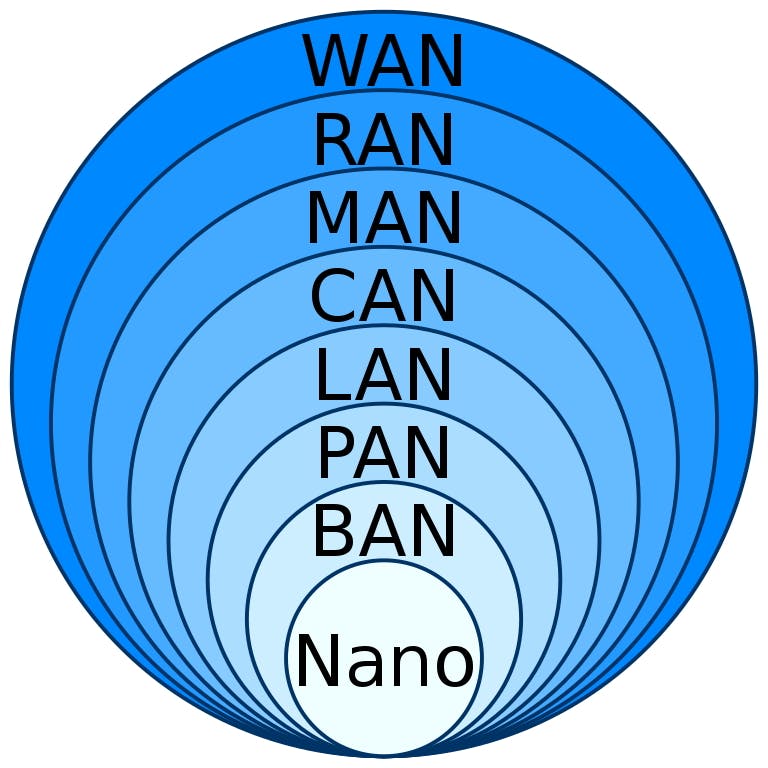
LPWAN is a technology category within the WAN (wide area network) spacial context. The initials stand for Low-Power Wide Area Network (or Networking). In a traditional network, continuous connectivity is expected between the network infrastructure and connected devices. In LPWAN, devices connect momentarily – just enough to transmit a short burst of data.
All-in-one RWOB
MAXIMIZE YOUR SECURITY OPERATIONS CAPABILITIES
Upgrade your security operations effectiveness through Security Technology Strategic Planning. Provably get more for your company's security technology investment.
★ ★ ★ GET NOTIFIED! ★ ★ ★
SIGN UP to be notified by email the day a new Real Words or Buzzwords? article is posted!
Real Words or Buzzwords?
The Award-Winning Article Series
#1 Proof of the buzzword that killed tech advances in the security industry—but not other industries.
#2 Next Generation (NextGen): A sure way to tell hype from reality.
#3 Customer Centric: Why all security industry companies aren't customer centric.
#4 Best of Breed: What it should mean to companies and their customers.
#5 Open: An openness scale to rate platforms and systems
#6 Network-friendly: It's much more than network connectivity.
#7 Mobile first: Not what it sounds like.
#8 Enterprise Class (Part One): To qualify as Enterprise Class system today is world's beyond what it was yesterday.
#9 Enterprise Class (Part Two): Enterprise Class must be more than just a top-level label.
#10 Enterprise Class (Part Three): Enterprise Class must be 21st century technology.
#11 Intuitive: It’s about time that we had a real-world testable definition for “intuitive”.
#12 State of the Art: A perspective for right-setting our own thinking about technologies.
#13 True Cloud (Part One): Fully evaluating cloud product offerings.
#14 True Cloud (Part Two): Examining the characteristics of 'native-cloud' applications.
#15 True Cloud (Part Three): Due diligence in testing cloud systems.
#16 IP-based, IP-enabled, IP-capable, or IP-connectable?: A perspective for right-setting our own thinking about technologies.
#17 Five Nines: Many people equate high availability with good user experience, yet many more factors are critically important.
#18 Robust: Words like “robust” must be followed by design specifics to be meaningful.
#19 Serverless Computing – Part 1: Why "serverless computing" is critical for some cloud offerings.
#20 Serverless Computing – Part 2: Why full virtualization is the future of cloud computing.
#21 Situational Awareness – Part 1: What products provide situational awareness?
#22 Situational Awareness – Part 2: Why system designs are incomplete without situational awareness?
#23 Situational Awareness – Part 3: How mobile devices change the situational awareness landscape?
#24 Situational Awareness – Part 4: Why situational awareness is a must for security system maintenance and acceptable uptime.
#25 Situational Awareness – Part 5: We are now entering the era of smart buildings and facilities. We must design integrated security systems that are much smarter than those we have designed in the past.
#26 Situational Awareness – Part 6: Developing modern day situational awareness solutions requires moving beyond 20th century thinking.
#27 Situational Awareness – Part 7: Modern day incident response deserves the help that modern technology can provide but doesn’t yet. Filling this void is one of the great security industry opportunities of our time.
#28 Unicity: Security solutions providers can spur innovation by envisioning how the Unicity concept can extend and strengthen physical access into real-time presence management.
#29 The API Economy: Why The API Economy will have a significant impact on the physical security industry moving forward.
#31 The Built Environment: In the 21st century, “the built environment” means so much more than it did just two decades ago.
#32 Hyper-Converged Infrastructure: Hyper-Converged Infrastructure has been a hot phrase in IT for several years, but do its promises hold true for the physical security industry?
#33 Software-Defined: Cloud-computing technology, with its many software-defined elements, is bringing self-scaling real-time performance capabilities to physical security system technology.
#34 High-Performance: How the right use of "high-performance" can accelerate the adoption of truly high-performing emerging technologies.
#35 Erasure Coding: Why RAID drive arrays don’t work anymore for video storage, and why Erasure Coding does.
#36 Presence Control: Anyone responsible for access control management or smart building experience must understand and apply presence control.
#37 Internet+: The Internet has evolved into much more than the information superhighway it was originally conceived to be.
#38 Digital Twin: Though few in physical security are familiar with the concept, it holds enormous potential for the industry.
#39 Fog Computing: Though commonly misunderstood, the concept of fog computing has become critically important to physical security systems.
#40 Scale - Part 1: Although many security-industry thought leaders have advocated that we should be “learning from IT,” there is still insufficient emphasis on learning about IT practices, especially for large-scale deployments.
#41 Scale - Part 2: Why the industry has yet to fully grasp what the ‘Internet of Things’ means for scaling physical security devices and systems.
#42 Cyberspace - Part 1: Thought to be an outdated term by some, understanding ‘Cyberspace’ and how it differs from ‘Cyber’ is paramount for security practitioners.
#43 Cyber-Physical Systems - Part 1: We must understand what it means that electronic physical security systems are cyber-physical systems.
#44 Cyberspace - Part 2: Thought to be an outdated term by some, understanding ‘Cyberspace’ and how it differs from ‘Cyber’ is paramount for security practitioners.
#45 Artificial Intelligence, Machine Learning and Deep Learning: Examining the differences in these technologies and their respective benefits for the security industry.
#46 VDI – Virtual Desktop Infrastructure: At first glance, VDI doesn’t seem to have much application to a SOC deployment. But a closer look reveals why it is actually of critical importance.
#47 Hybrid Cloud: The definition of hybrid cloud has evolved, and it’s important to understand the implications for physical security system deployments.
#48 Legacy: How you define ‘legacy technology’ may determine whether you get to update or replace critical systems.
#49 H.264 - Part 1: Examining the terms involved in camera stream configuration settings and why they are important.
#50 H.264 - Part 2: A look at the different H.264 video frame types and how they relate to intended uses of video.
#51 H.264 - Part 3: Once seen as just a marketing term, ‘smart codecs’ have revolutionized video compression.
#52 Presence Technologies: The proliferation of IoT sensors and devices, plus the current impacts of the COVID-19 pandemic, have elevated the capabilities and the importance of presence technologies.
#53 Anonymization, Encryption and Governance: The exponential advance of information technologies requires an exponential advance in the application of data protection.
#54 Computer Vision: Why a good understanding of the computer vision concept is important for evaluating today’s security video analytics products.
#55 Exponential Technology Advancement: The next 10 years of security technology will bring more change than in the entire history of the industry to now.
#56 IoT and IoT Native: The next 10 years of security technology will bring more change than in the entire history of the industry to now.
#57 Cloud Native IoT: A continuing look at what it means to have a 'True Cloud' solution and its impact on today’s physical security technologies.
#58 Bluetooth vs. Bluetooth LE: The next 10 years of security technology will bring more change than in the entire history of the industry to now.
#59 LPWAN - Low-Power Wide Area Networks: Emerging IoT smart sensor devices and systems are finding high-ROI uses for building security and safety.
#60 Edge Computing and the Evolving Internet: Almost 15 billion personal mobile devices and over 22 billion IoT devices operating daily worldwide have shifted the Internet’s “center of gravity” from its core to its edge – with many implications for enterprise physical security deployments
#61 Attack Surface: (Published as a Convergence Q&A Column article)An attack surface is defined as the total number of all possible entry points for unauthorized access into any system.
#62 Autonomous Compute Infrastructure: We’re on the brink of a radical new approach to technology, driven by autonomous operations.
#63 Physical Security Watershed Moment: We have reached a juncture in physical security technology that is making most of our past thinking irrelevant.
#64 Access Chaos: For 50 years we have had to live with physical access control systems that were not manageable at any large scale.
#65 AI and Automatiom: Will engineering talent, business savvy and capital investment from outside the physical security industry bring technology startups that transform reactive security to proactive and preventive security operations?
#66 Interoperability: Over the next five years, the single greatest determinant of the extent to which existing security industry companies will thrive or die is interoperability.
#67 AI Model : One key factor affects the accuracy, speed and computational requirements of AI
#68 Interoperability – Part 2: There are two types of security system interoperability – both of which are important considerations in the design of security systems and the selection of security system products.
#69 Interoperability – Part 3: There are two types of security system interoperability – both of which are important considerations in the design of security systems and the selection of security system products.
#70 Operationalizing AI: AI is not a product, but a broad category of software that enables products and systems to do more than ever before possible. How do we put it to good use?
#71 Shallow IT Adoption – Part 1: It’s not just about being IT compliant, it’s also about leveraging IT capabilities to properly serve the needs and wants of today’s technologically savvy customers.
#72 E-waste – an important security system design issue: Now e-waste is an important design issue not just because of growing e-waste regulations, but because educated designers can save enterprise security system customers a lot of money.
#73 LRPoE - Long Reach Power over Ethernet: A dozen factors have improved the business attractiveness of network cameras, making it more desirable to place cameras further from existing IT closets than the 328 foot limitation of standard Ethernet cable.
#74 NIST Declares Physical Access Control Systems are OT: Does it really mean anything that OT has joined the parade of labels (IT, IoT, and then IIoT) variously getting applied to security systems?
#75 Future Ready: Google sees the term "future-ready" trending up across many subject domains. But does that term apply to the physical security industry and its customers?
#76 Data KLiteracy: AI needs data. Thus, the ability of any department or division in an organization (including security) to use AI effectively depends on its ability to effectively obtain and utilize data – including security.
#77 Security Intelligence (upcoming): AI brings two kinds of intelligence to physical security systems – people bring the third.
More to come about every other week.

It can be challenging for organizations to adopt innovative IoT technology in a secure manner and integrate it into their existing legacy – but still functional – physical security or building controls systems infrastructure. A recent technology evaluation project required me to examine a portion of the smart IoT sensor landscape regarding sensor technologies that are suitable for use in a variety of building safety and security monitoring applications.
This article is about network technology, but first I want to address the reason that such technology is now important to us.
Time-Critical Personnel Risks
Over a decade ago several clients asked for help in dealing with critical personnel risk situations which, at that time, could only be dealt with using people as there were no workable technologies for such situations.
One of them was a rare lone worker risk among the most valuable long-term company employees working in one of their chemistry labs. On occasion, an employee would work past the end of the afternoon shift to complete a multi-hour timed test in an important series of tests that all must be run within specific time frames. One of the senior, and very dedicated employees, had worked a few hours past midnight and had a heart attack and collapsed onto the floor. He was discovered at the start of the day shift by another employee, who made the 911 call that fortunately saved his life.
A risk assessment prompted the launch of a company-wide wellness campaign – now a common element of most medium and large company’s health programs. The also instituted a firm two-person requirement so that no individual would be in a lone worker situation.
However, in some cases, the lone worker situation can occur unintentionally. Thus, increased indoor night security officer checks were also instituted.
The use of video analytics was considered as a possible solution but soon was dismissed because the cost of video coverage for 100% of facility areas was astronomical, and the state of video analytics at the time would have resulted in hundreds of nuisance alarms.
Now, however, such risk situations can be easily and affordably monitored with no nuisance alarms and without privacy invasion. An example from Orion Entrance Control is its small-sensor radar-based human presence and vital sign detection that can determine breathing rate and heart rate, detect coughing and sneezing, and recognize falls or too-long periods of body stillness. In some environments all of those factors can be critically important. I was in a 15-story building once where an emergency evacuation was conducted due to an unusual cleaning chemical spill whose fumes were being sent throughout the building by the HVAC system. There was no way to confirm a full evacuation until emergency responders arrived and donned hazmat suits. Luckily there were no remaining occupants, but it took over a half hour to determine that fact. I can’t help but think about how first responders to the World Trade Center towers on 9/11 would have been able to save more people, if they could have accurately pinpointed the locations of every individual in the buildings and prioritized those whose vital signs or stillness indicated they were likely suffering from severe smoke inhalation and could not evacuate on their own. I believe that the effectiveness of this and other sensor systems will drive significant adoption of such sensors in the same way that modern deep-learning based video analytics has done for video deployments in the retail marketing space. Like with video analytics, in addition to the personal safety and security aspects, there are also many business operational benefits to gain from building sensor data. Smart Sensor Communications I also found products with an amazing array of communications capabilities, including one product whose data communication options were: RS-232, RS-422, Wired Ethernet (10, 100, 1 Gbps, 10 Gbps), Wi-Fi, Bluetooth and Bluetooth LE, Cellular (3G, 4G LTE, 4G, and 5G), LoRa, and LoRaWAN. I was surprised to see the support for 10 Gbps communications on one of the gateway systems, until I saw the number of devices that the gateways could support, and what a large sensor deployment could require when configured to provide thermal or 3-D mapping images in for verification of alerts which might be required as forensic evidence in some types of incidents. Another company covered the same overall set of communications technologies, but did so using a number of products whose differences were mainly in the small set of communication capabilities each product offered. Each set of communication options was designed to fit use cases in specific business and industry segments. This lowered the product costs, as they didn’t need to be general purpose devices. Other companies weren’t so specific about communications capabilities, and would state, for example, “Ethernet, Wi-Fi and LPWAN.” That, of course, left me with questions. What wired networking speed is required and are both frequencies of Wi-Fi supported (2.4 GHz and 5 GHz)? Furthermore, what LPWAN technologies are supported? LPWAN In a traditional network, continuous connectivity is expected between the network infrastructure and connected devices. In LPWAN, devices connect momentarily – just enough to transmit a short burst of data. Some devices may even go to sleep until an input signal arrives. That enables, for example, small sensors to run up to 20 years on a single coin battery. Traditional wired or wireless networking energy requirements would drain such a battery in a matter of hours. The “low power” in LPWAN refers to a network of low power devices. There are also special communications protocols that allow multiple uses of sensors, whose data push feeds can be subscribed to by multiple devices and systems. This is something new to the physical security industry, as security systems haven’t previously been designed to publish data anywhere except a central monitoring point or security operations center (SOC). IoT Messaging Protocols The People Counter is a video-based stereo-vision device from Axis Communications, always an industry leader. The People Counter supports the MQTT protocol, and is evidence that physical security technology stakeholders need to pay attention to the Industrial IoT networking and data exchange landscape. Figure 1 below, from Wikimedia Commons, illustrates the spacial classification of various networks, most if not all of which technology-focused readers will have seen. Each of these network classification categories contains numerous networking technologies, many of which tomorrow’s physical security systems will include either by way of device deployment or systems integration. Real Words or Buzzwords? will continue to provide information about the involved technologies and terminology, including the MQTT protocol, so that our forays into the world of Industrial IoT can have more clarity than our earlier industry experiences with Information Technology had.
While researching smart sensor technology I found dozens of smart sensors and smart sensor systems that support a variety of communications technologies. Comparing products was challenging due to the lack of uniformity in how communication capabilities were specified. There were also errors in documentation, such as where Bluetooth was wrongly used to refer to a product that used Bluetooth Low Energy (BLE) for data transmission. The two are not the same and are not directly compatible. That prompted my recent article titled, “Bluetooth vs. Bluetooth BLE.”
LPWAN is a technology category within the WAN (wide area network) spacial context. The initials stand for Low-Power Wide Area Network (or Networking). At first glance that would seem to be a self-contradicting term. How could a wide area network be classified as low-power? One difference is that an LPWAN uses entirely different networking technology (there are several) than a traditional WAN.
“MQTT is a Client Server publish/subscribe messaging transport protocol. It is light weight, open, simple, and designed so as to be easy to implement. These characteristics make it ideal for use in many situations, including constrained environments such as for communication in Machine to Machine (M2M) and Internet of Things (IoT) contexts where a small code footprint is required and/or network bandwidth is at a premium.” (From the official MQTT 3.1.1 specification, which has not advanced to version 5.) The MQTT open specifications are managed by OASIS, one of the most respected, non-profit international standards bodies.