Having worked with this tool now for almost eight years, I can tell you that its simplicity hides its power. At every company where we have simply discussed it, security managers couldn’t stop applying it in their thinking, even when we had no formal program in place.
This particular Security Management Maturity Model is based upon the many maturity models 1 that have grown out of the original research performed at Carnegie Mellon University.
Although the original Maturity Model work was done in relation to software development and IT security programs, this model presented here applies to physical, IT, corporate and safety programs.
You can rate your security program overall or any part of it, and even rate companies who are offering you safety and security products and services, according to this model.
How to Use This Model in 90 Seconds
The chart below in Table 1 contains a Security Management Maturity Model. If no one has been assigned overall responsibility for security, that would be Level 0. To rate your organization, program or group, read Level 1 of the chart. If not all of the Level 1 requirements are met, the organization, program or group being rated is at Level 0 (not yet on the chart).
If all of the Level 1 characteristics exist, examine Level 2, and so on.
The rating to assign is the highest level at which your organization matches or exceeds all of its characteristics.
It is rare for an organization’s security program or security department to be at Level 4 or higher if it has not been following a model similar to this one.
Further Study
Studying this model will take much more than 90 seconds, but is well worth the time.
Drilling Down for Implementation
The status of implementing any level (or any one of its elements) can also be assessed according to the following criteria:
- Unconsidered: The level or element has not yet been given any consideration
- Identified: The level or element has been identified as a requirement for your organization or department or program.
- Planned: The related processes and procedures have been developed.
- Implemented: The processes and procedures are actually in use.
- Verified: The results of the processes and procedures are audited periodically.
- Integrated: Circumvention of processes and procedures is insignificant.
Note that the above criteria are useful simply for assessing the status of a level or element and measuring progress as things move along. They are not maturity measurements or part of the model.
What I like about this Security Management Maturity Model is that it is written in plain language and can be used by CEOs, CFOs, and other senior management security stakeholders.
With this tool in hand you can:
- Determine your organization’s or departments security management maturity
- Set a maturity target
- Develop a prioritized outline of what to put in place to get there
It is an excellent tool for a corporate Security Steering Committee or Security Council.
I hope it expands your thinking about security as much as it has ours.
I am also interested in hearing your feedback about this tool either by contact form or email to me.
Best regards,
Ray Bernard
P.S. For a positive message to those who find their security departments or programs are at Level 1 or Level 2, see the Bonus Thought section below the Security Management Maturity Model table.
Table 1. Security Management Maturity Model 3 (Bold text is intended to emphasize the differences between one level and another.)
| Level | Name | Description and Characteristics | Results and Objectives |
|---|---|---|---|
| Level 1 | Initial | Security is not acknowledged as an important aspect of the organization. The absence of incidents is the result of luck or individual efforts. | The occurrence of incidents invariably leads to the maximum impact that could be expected. |
| Level 2 | Acknowledged Also described as: Intuitive but not documented |
Security is acknowledged as an important aspect of the organization. The absence of incidents is the result of luck or some individual or organizational efforts.
|
The occurrence of incidents doesn’t always lead to the maximum impact that could be expected.
The results of the organizational security efforts fade with time. Thus security ROI is deceptive and in the long term turns out to be less than expected. |
| Level 3 | Defined
Also described as: |
Security is acknowledged as an important aspect of the organization. The absence of incidents is the result of luck and continuous organizational efforts.
|
The occurrence of incidents normally doesn’t lead to the maximum impact that could be expected.
The results of the organizational efforts are permanent. Security ROI is as expected. |
| Level 4 | Controlled | Security is acknowledged as an important aspect of the organization.The absence of incidents is the result of continuous organizational efforts.
|
The occurrence of incidents virtually never leads to the maximum impact that could be expected.
The results of the organizational efforts are permanent and improve over time. The breadth of security ROI increases over time. Security is appropriate for the business sector. |
| Level 5 | Optimized (Continuously Improving) |
Security is acknowledged as an important aspect of the organization.The absence of incidents is the result of continuous organizational efforts.
|
The occurrence of incidents doesn’t lead to the maximum impact that could be expected.
The results of the organizational efforts are permanent and improve over time. Security operations become more efficient over time, providing an increasing return for the ongoing security investment. Security is well-aligned with the business. |
Bonus Thought (Back to document reference)
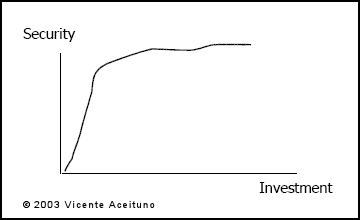
A study at Carnegie Mellon University 4 showed that the more you spend the less difference it makes on your security, as depicted in Figure 1 below 5 . This means the largest security gains per dollar spent on security will be at Security Management Maturity Model Levels 1 and 2.
So if you were disheartened to have a rating that was low on the scale, take heart in the fact that the next security dollars you spend have the potential for providing you the greatest return on security investment!
Figure 1. Early Security Investments Provide the Greatest Return
Footnotes
http://tinyurl.com/sticky-minds-maturity-models
Back to document reference
2 Capability Maturity Model® and CMM® are registered in the U.S. Patent and Trademark Office by Carnegie Mellon University
Back to document reference
http://www.slideshare.net/vaceitunofist/security-maturity-model
For an in-depth look at an Information Security Management Maturity Model along the lines of the table above, download the 98-page standard ISM3 version 2.00 from: http://www.lean.org/FuseTalk/Forum/Attachments/ISM3_v2.00.pdf
Back to document reference
4 Carnegie Mellon University (2000) “The Survivability of Network Systems: An Empirical Analysis”
Back to document reference
5 From a presentation by Vicente Aceituno titled, “Return on Security Investment”, available on SlideShare:
https://www.slideshare.net/vaceitunofist/rosi-16620354
Back to document reference

