by Ray Bernard
Below is a color version of an illustration about physical security and IT security collaboration touch points, from Chapter 12 of the book, Security Convergence: Managing Enterprise Security Risk, by Dave Tyson.
This was one of the first books published on security convergence, and its content remains valid today.
Figure 12-1. Enterprise convergence points.
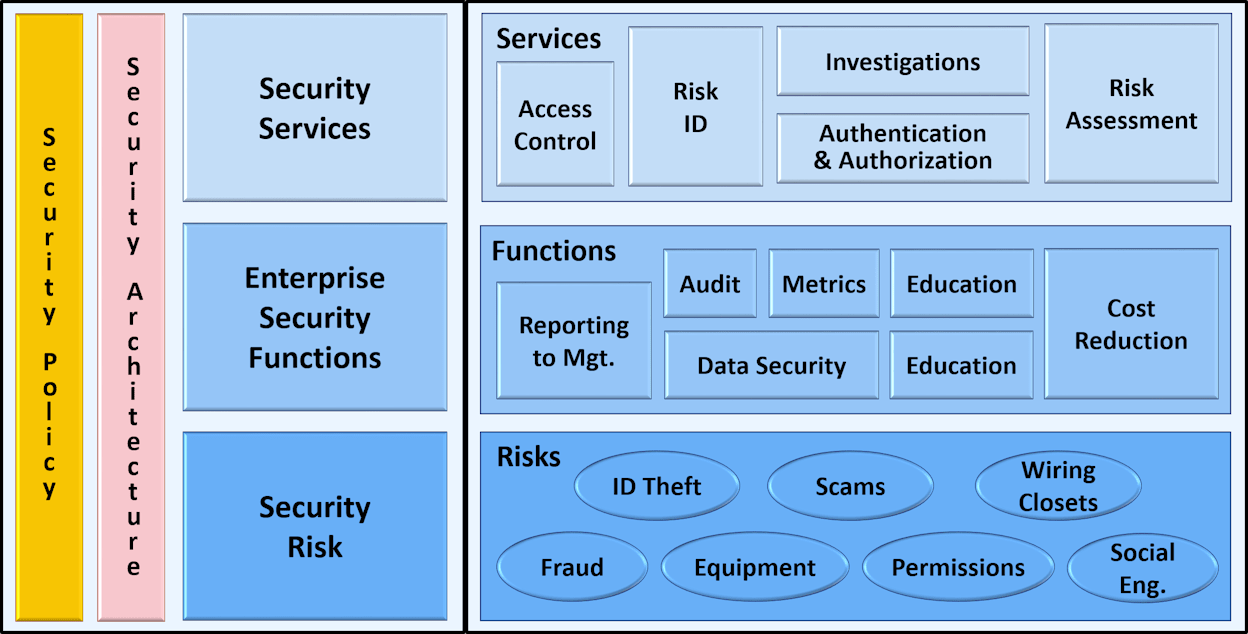
Physical Security and IT Security Collaboration
You won’t find a category for physical security technology on that diagram, because it outlines collaboration points from the enterprise risk perspective. You will see security services that are common to both IT and physical security, including Access Control, Risk Identification, Authentication and Authorization, and Investigations. While the technologies involved are different, their purposes are the same.
This book is extremely valuable for physical security managers and directors, as it presents the convergence picture as management sees it.
Physical Security and Information Technology
Security technology convergence, which is a separate but related topic, is covered by my book, Security Technology Convergence Insights, which covers the incorporation of information technology into physical security systems and products. Today, all industries and professions are experiencing the emergence of information technology into the products, tools and systems they use. Security technology is advancing at an exponential rate, due to the exponential advancement of information technology, and high rate at which new technologies are emerging.
For more information on the rate of security technology advancement, jump to this article: The Increasing Pace of Technology Advancement.

