How to Validate
Your Security Program
15 Ways to Rate Your Program
WHY VALIDATE? The top 5 reasons to validate your security program.
Your Security Program Should Be:
#1 – Authoritative
#2 – Defensible
#3 – Qualified
#4 – Justifiable
#5 – Proven
#6 – Well-Supported
#7 – Official
#8 – Robust
#9 – Relevant
#10 – Well-Founded
#11 – Accepted
#12 – Effective
#13 – Viable
#14 – Substantiated
#15 – Successful
By Ray Bernard PSP, CHS-III
Note: This is the eighth of a multi-part series that provides 15 important perspectives from which to validate your Security Program. If this is the first article you have seen in this series, please read the WHY VALIDATE? introductory article before launching into the validation steps.
An attribute is a quality or feature regarded as a characteristic of something. What we are calling the “15 Validation Attributes” are 15 characteristics that you can use to validate your security program.
Validation Attribute: Robust
Definition:
- (of an object) sturdy in construction
- (of a process, system, organization, etc.) able to withstand or overcome adverse conditions
A robust security program is one that is able to stand up to adverse conditions and still provide the intended degree of asset protection, whether the assets are property, materials, people, electronic data, or critical processes.
There are two complementary best-practice approaches that can be used to provide very robust security, and the concepts are the same for physical and IT security:
- Layered Security
- Defense in Depth
These two approaches can be effectively applied to any type of security program, whether for electronic information protection, physical security protection, or executive personnel protection.
Confusion About Layers and Defense in Depth
There is a significant amount of material to be found on the Internet about these two topics. Quite a few books have chapters dedicated to the subject. Unfortunately, for most of the material, each author presents a slightly different picture of layered security and defense in depth than the other authors do. Additionally, many authors say that they are the same thing, while other authors insist that layered security and defense in depth are not the same thing. In writing this article I checked the book material against print magazine columns and articles, and material online, and I found that the book material did a much better job of explaining the terms. Still, the distinctions between the two are not always clear. One purpose of the sections that follow below is to clarify the difference between Layers of Security and Defense in Depth, as they do not really refer to the same thing.
Layers of Security for Facilities
Layers of security refers to the series of protected zones in a facility, starting at the outside and working in, with each layer having one or more protective measures in place. This is what the Figure 1 illustration shows. It is an oversimplification, because unless your facility is built like the Pentagon, its design is not based upon concentric rings of corridors. Yet the idea of establishing multiple protected zones, through which an adversary must advance to reach any critical assets, is a workable security design approach and can usually be achieved with slight or no building modification. The same principle applies with regard to information systems, where multiple layers of security controls are placed throughout an information system, requiring an adversary to penetrate them all in order to reach protected information assets. This is shown in Figure 2.
Figure 1. Facility primary layers requiring protection
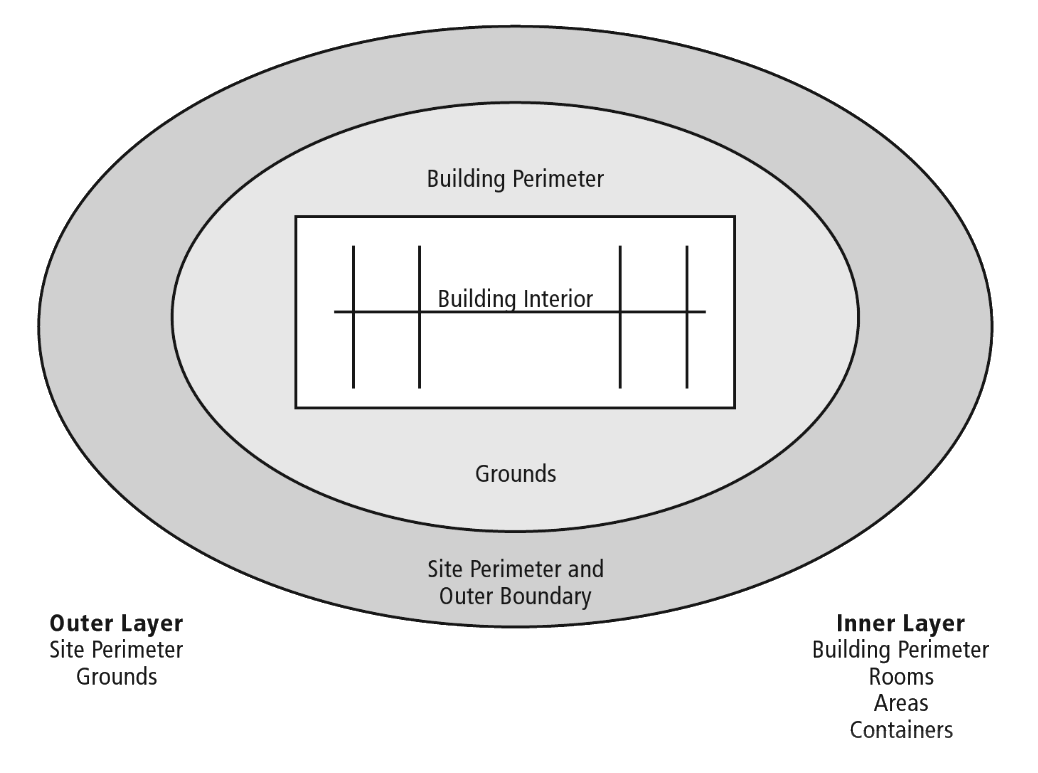
Source: The Manager’s Handbook for Corporate Security
In Figure 1 the Outer Layer consists of the site perimeter and the grounds and outer boundary of the property. The Inner Layer consists of the building perimeter and the rooms, areas and containers within the building. The perimeter of the Outer Layer may have a gated fence, and the grounds may contain a parking lot. Within the Outer Layer there may be additional layers of protection on the grounds, such as bollards and shrubbery to keep vehicles from driving up next to the building and to protect items such as transformers, and water and gas piping and controls.
The Inner Layer begins at the building outer wall. Within the building there can be several additional layers of security. For example, building entry doors may lead to general use hallways, with additional access-controlled doors within the hallways to provide separation for functional areas such as accounting, sales and marketing, Human Resources, and senior management offices. Rooms within each office area may have access-controlled doors to restrict access to each specific room.
Layers of Security for IT
Figure 2 below conceptualizes layers within an information system, showing where security controls can be utilized to create zones of protection. For example, firewalls and routers are used to establish perimeter layer protection against malicious attempts to access the network. If properly configured these devices would stop nearly all of the malicious traffic, leaving the other layers of protection to deal with the smaller amount of malicious traffic that does get through. Network layer defenses would be established using additional firewalls, routers, intrusion prevention systems, and other controls. The remaining layers would each have appropriate protections applied, including strong user credentials, encryption, anti-virus, and so on.
Figure 2. Information system layers requiring protection

Source: RBCS
Defense in Depth
Whether physical or logical systems are involved, defense in depth consists of using multiple defensive mechanisms at each layer of security, with each defensive mechanism providing a different defensive function. The idea is that if one defensive mechanism fails, others should succeed.
[/raw]
Cost effectiveness is served by making the security measures stronger the closer a layer is to protected assets. Completely hardening every aspect of a facility, or of an information system, is not cost-feasible. This is why usually a few different types of security are used in the perimeter layer, and a greater number of security measures are used closer to the protected assets.
Multiple security measures can provide highly effective protective and response capabilities, and also provide redundancy so that if one level or layer of security fails or is bypassed, others are still in effect. For example, a highly confidential formula for a high-performance lubricant (or a research sample of it) could be safeguarded by the following multiple security measures:
- A high-security electronic combination-lock safe in its own room
- A two-person safe access rule
- A safe room access log
- Both in-safe and external logs of contents added or removed
- Biometric access authentication
- One-time use safe combinations
- Two-person rule enforced by the access control system
- Live video surveillance camera coverage
- PIR motion detection
- Video-based motion detection
- Video recording
- Motion-alerts initiating video observation by a monitoring security officer
- Card reader access control for the room and the hall leading to the safe room
- Security officer patrols
- Strong background checks on the personnel who are given access to the area and to the safe itself, including the locksmith company personnel who install and service the safe
- Firm policies governing the use of the safe and its access
- Periodic audits of safe access records.
There would be multiple layers of high protection: the safe room, the hallway leading to the safe room, the floor of the building on which the safe room is located.
Few areas or assets will require this many layers and levels of protection, but all critical assets should have an appropriate number of protection layers and levels established and documented.
A good approach is: (a) identify the layers of protection available, or create them; (b) determine which types of security measures security should be applied to each layer (designing defense in depth to accommodate one or more security measure failures); (c) develop appropriate threat (and security failure) scenarios and make response plans for them.
Levels of Security
To facilitate discussions, I use the term “levels of security” to refer to the defense-in-depth measures applied to any particular protection layer. For example, you can say, “We have three levels of security for this layer, and five levels of security for the next layer in.” It’s a simple way to roughly compare the degree of robustness between layers. Additionally, you could say, “We need more levels of security for this layer, because not all of the potential failure scenarios are covered.” You can make a table listing the layers of security and which levels of security are applied. It’s a useful term that facilitates discussion and documentation.
Fully Implementing Defense in Depth
Closely associated with the concept of defense in depth are four key functions of security operations:
- Deter (send them away)
- Detect (find out where they are)
- Delay (slow them down)
- Respond (assess the situation and address the attack)
Here is how this could work for facilities.
Deterrence. The Outer Layer may have fence signage warning trespassers that the fence encloses private property. There may be clearly visible outdoor surveillance cameras covering the grounds up to the fence line. There may be motion-activated security lighting no the outside of the building. Access controlled vehicle and pedestrian gates can deny access to unauthorized individuals. These and other measures will have some degree of a deterrent effect.
Detection. The earlier the detection of attempted unauthorized entry, the better. Fence intrusion detection systems provides early warning, and can be used to trigger additional deterrent measures such as lighting and recorded announcements to warn off the trespassers. After normal business hours, indoor motion detectors in unoccupied building areas can be used to alert security personnel of unauthorized individuals in those areas.
Delay. The idea behind delaying an adversary is to gain enough time to assess the situation and prepare an appropriate response.
Response. Perhaps security officers would respond by using PTZ cameras to record the activities close up (zoomed in). Perhaps part of all of the facility will be locked down. Perhaps police should be summoned. Maybe all of these things should be done.
The same Deter, Detect, Delay and Respond functions can be worked out for information security.
Robust Security
A robust security program is one whose various program elements can stand up to adverse conditions and still provide the intended degree of asset protection. How robust is your security program? Use the validation steps to get a clear picture.
Validation Steps
These validation steps are conceptual and can be applied to facilities and to information systems.
More detailed steps are provided in separate documents below, as Facility Validation Steps and Infosec Validation Steps.
Step 1. Identify the critical assets and the pathways to them.
Step 2. Document the layers and levels of protection that exist along the paths to the critical assets.
Step 3. Determine if improvements should be made.
You can perform these steps iteratively, initially starting with the few most critical assets. The next most critical assets are likely to be using a subset of what you worked out for the few most critical assets, so the work is easier from that point on.
Attending to the robustness of your security program elements improves their resilience, something that managers and executives have a better understanding of these days.
Download More Detailed Steps
![]() Facility Security Validation Steps
Facility Security Validation Steps
RBCS-Facility-Security-Program-Validation-Steps-Robust-v1-0.pdf
![]() Information System Security Validation Steps
Information System Security Validation Steps
Please check back in early 2023, as I am revising the Information System Security Validation Steps to simplify them a little bit, and get feedback before I post them. If you would like to be reminded when I post the updated steps, I’ll send you a note or just email the document to you (see below).

