Security program elements, and the various risk factors they address, seem obvious or “natural” to experienced security practitioners. Yet most non-security personnel, including security stakeholders who regularly interact with security, have little insight into an organization’s security risk picture. What’s more, the impressions of the security function that non-security personnel have result from their exposure to visible security elements such as access cards, logon credentials, access-controlled doors, and patrolling security officers. The visible elements don’t even constitute the tip of the iceberg.
This is why providing small insights into the organization’s security risk picture and the related aspects of a security program is very effective in filling the vacuum of what security is all about. These small bits of information can significantly elevate the importance of security and its role in protecting organizational assets.
Educational Posters
RBCS consultants have created several types of client-specific informational posters that have been of high interest to functional area managers and other personnel who interact with Security. Three of them are:
- Next Generation Security Qualifications Chart
- "What We Do" Security Program Risks Chart
- Cross-Functional Security Success Chart
Next Generation Security Qualifications Chart
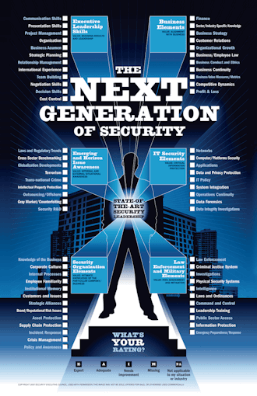
The Next Generation Security Qualifications Chart is a poster developed by the Security Executive Council based upon its research into the skills and knowledge required by the today's security leaders.
Filling out and saving this chart, printing it as a large poster, and mounting it in or near a security office or security personnel cubicle makes an impressive and enlightening educational piece.
"What We Do" Security Program Risks Chart
A What We Do poster usually elicits comments like, "Wow - I had no idea you guys did all this!" Including the "Job of Security" description at the top of the poster really helps provide a clear concept of security's role (whether you call it security's "job", "purpose" or "mission"). You can create your own poster easily enough by making a chart in Word® or Excel® and printing it out as a 24" x 36" poster.
An example format is provided below. If you like, you can include a security logo, company logo or photo in the title area, as shown. If the list is very long, you can use a four-column format so that you have a pair of Risk/Security Program Element columns.
| WHAT WE DO | |
|---|---|
| The job of security is to reduce security risks to acceptable levels, at an acceptable cost. |
|
| Risk | Security Program Element |
Cross-Functional Security Success Chart
The Cross-Functional Security Success Chart is another valuable tool for showing the support provided to Security by other functional areas. It is important to acknowledge and validate such efforts, and to make them known to others. This chart is like the "What We Do" chart, except that it contains only those functions where other functional areas perform some or all of the function. An example format is below. Of course this example is only a partial listing. Generally, the longer the listing the better.
In most cases, when we display or post (corporate intranet) such a poster, we also issue letters or memos of commendation to each contributing individual and their supervisors and managers, with a copy to HR for their personnel file.
| CROSS-FUNCTIONAL SECURITY SUCCESS ï THANK YOU! ð |
|||
|---|---|---|---|
| Risk | Security Program Element | Functional Area | Since |
| Corporate liability for mistakes by insufficiently trained security personnel | Co-Op Education and Training Program | Human Resources | 2006 |
| Workplace misconduct and violence by personnel with criminal history | Background Investigations | Human Resources | 2004 |
| Printed confidential, sensitive or privacy-controlled documents unprotected due to lack of proper classification. | Document Classification Program | Corporate IT | 2009 |
| Mishandling of confidential, sensitive or privacy-controlled documents due to lack of information security awareness | Information Security Awareness Training | Corporate IT | 2009 |
| Printed confidential, sensitive or privacy-controlled documents unprotected due to lack of proper classification. | Document Classification Program | Corporate IT | 2009 |
| Electronic evesdropping via user wireless headsets and conference room wireless microphones | Electronic Communications Security | Corporate IT | 2010 |
| Security department incident and investigations data accessed by unauthorized individuals. | Computer & Network Security | Corporate IT | 2009 |
| Personnel serious injury and critical asset loss or damaged due to unsupressed facility fire | Fire Detection and Suppression Systems | Industrial Safety Program | 1990 |
| Unauthorized access through security doors, gates or into safes and vaults | Door/Gate/Safe Lock & Key Management | Facilities Department | 1996 |
| Unauthorized entry into facilities and their protected areas | Security Door Maintenance | Facilities Department | 1998 |
| Serious physical injury to on-site personnel during emergency incident or crisis situation | Security & Safety Emergency Response Procedures | Industrial Safety Program | 2008 |

