Don’t make common mistakes when talking about cloud services on the show floor.
This is an EXPANDED VERSION of an article originally published in Security Dealer & Integrator magazine, August 2016, titled “Addressing Cloud Risks”. This expanded article includes key mistakes vendors have been making on trade show floors.
First, to understand the mistakes being made in trade show discussions, you have to understand why customers are less impressed at the shows than they used to be, and how the mindset they bring to sales discussions has changed. Then it is easier to see what mistakes are being made in discussions about the cloud.
Short on time?
Jump right to: Show Preparation.
Get the three Key Questions to prepare for the show.
There are two megatrends that are disruptively impacting many industries – including security – and they both amplify the risks that integrators and cloud offering providers have relating to cloud-based services (as well as any leading edge technology). They impact the design, manufacture and delivery of any cloud-based or cloud-assisted electronic physical security systems technologies. They are:
- Continually accelerating widespread technology advancement; and
- An epochal never-happened-before shift in control of the seller-customer marketplace.
Technology advancement is a given, and we all know this, but we are not good at grasping the ever-accelerating aspect of it, partly because the pace of the security industry advancement is relatively slow compared to other industries. We head to the 2016 trade shows looking for new vendor offerings for biometrics, video and video analytics, expecting only a few significant improvements.
While, for example, in the flimmaking industry Lytro Cinema is at industry shows introducing its 755 megapixel, 300 frames-per-second light field camera, which has light sensors just over 18″ wide (contrast with a half-inch sensor for security megapixel cameras). Lytro Cinema’s camera has over a million micro-lenses in its huge lens, capturing light-ray information (as it travels to and bounces off objects in the scene) recording all light ray impacts with still and moving scene contents. The amount of data captured is equivalent to about 75 MB per image pixel, an amazing feat at 300 frames per second.
A light field camera doesn’t capture 2-D bitmap images of the camera’s field of view. Instead it captures light ray information in a 3-D perspective, which allows video editors to play back the light rays digitally and using software adjust camera focus, aperture, and other aspects during playback. The adjusted light ray stream is then exported as a 2-D or 3-D video.
The captured raw light ray data can be sent to the cloud where cloud-based processors enable digital video editing from a workstation anywhere. A scene can be played back applying software tools for changing the focus and depth-of-field. Because the scene contains digital objects located in a 3-D space, not a flat set of pixels, object colors and the effect of light on them can be changed with complete photo-realism. Due to the amount of light information captured, the camera’s point of view can even be shifted 3° to the left or right to optimize the viewing angle.
Lytro Cinema’s product roadmap includes the capability to make the video camera’s point of view swing 360° around a center point in full 3-D by using just three or four cameras to simultaneously record the scene’s light rays from several angles. The roadmap also includes reducing the camera’s cost and form factor to match that of current-day 4K cinematic cameras. It is a very rapidly advancing area of video technology innovation.
It is easy to see how some aspects of light field video could capture activity in ultra-high resolution with significantly greater evidence value than what we have today. The security industry’s job will be to apply encryption and authentication technologies to such video to establish non-repudiation for evidence use. The big data technologies that exist today make this feasible, and those capabilities continue to be improved.
Industry Role Reversals
Just a few short years ago, security megapixel video was far advanced in resolution over the standard and HD video available from consumer and professional video equipment. Now the situation has flipped, with consumer product capabilities far outdistancing what the security industry is currently doing with video. Similarly, the Bosch automotive group started sharing video analytics used for self-parking and self-driving cars with the Bosch security systems group in 2013. In a few years all kinds of impressive video and video analytics will be available for security and business applications that will be arriving from other industries.
Diminishing Relevance
Now, at a point in time when advanced biometrics, cloud-based analytics, IoT and its big data avalanche, robotics, and other technology innovations are all right around the corner, the security industry is still five to ten years behind IT advancements. This shows when vendor personnel answer questions relating to IT topics, like cloud. A key risk security vendors face is remaining too far behind in advancing technologies, and becoming less relevant to customers. Customer expectations are set by advancing consumer technology that is outpacing the rate of advancement of entrenched security companies. We will continue to see new technology making its way into each upcoming security show from sources outside the industry.
Diminishing Sales Influence
We in the security industry also underestimate the ongoing marketplace shift, thinking of it as “commerce moving online”. However, there is much more to it than just a change to internet-based business transactions. There are momentous social dynamics at work, and how they are effecting every buyer-seller relationship is explained in the below below. Without realizing it, we are severely underestimating the impacts of the two major trends that are having the greatest impacts on security industry companies and customers.
Without understanding the risks and challenges of these trends and without reacting quickly enough to them, it is easy it to make deal-killing and company-crippling mistakes without ever realizing it, due to the marketplace shift explained below. The flip side is that with sufficient understanding of the challenges, it is just as easy to make deal-ensuring and company-advancing moves.
Marketplace Shift
An epochal marketplace shift is causing the 10,000-year-old “Age of the Seller” to be replaced by “The Age of the Customer®” – according to Jim Blasingame, author of the book The Age of the Customer (www.ageofthecustomer.com).
One of the most important things to know about the epochal marketplace shift is that it is an amplifier of many seller-side risk factors. Information in social media and online communities can have much greater reach and influence than a company’s own marketing messages do. That is phenomenally good when the online information is in a company’s favor; and phenomenally bad when the company is making mistakes and doesn’t know it. The worst-case situation is when the world (i.e. the company’s prospects and customers) finds out before the company does that it is making bad mistakes.
Blasingame explains, “For millennia, the marketplace dance between seller and customer was as beautifully simple as it was exquisitely effective, having at its nucleus three primary relationship elements:
- The product, controlled by the Seller.
- Information about the product, also controlled by the Seller.
- The buying decision, controlled by the Customer.
Then something happened that accomplished what no other event or innovation had been able to do for 10 millennia—the birth of a new Age.
In the new Age, the millennia-old marketplace dance is still beautifully simple. But the Age of the Customer has created a shift in who leads when the two dancers come together. Here’s the new paradigm:
- Products and services are still controlled by the Seller.
- The buying decision is still controlled by the Customer.
- Access to information, including customer experience, is now controlled by the Customer.
As you can see in the graphics below, the elements have shifted in terms of who controls of the relationship.”
Figure 1. The epochal permanent shift in control from seller to customer.
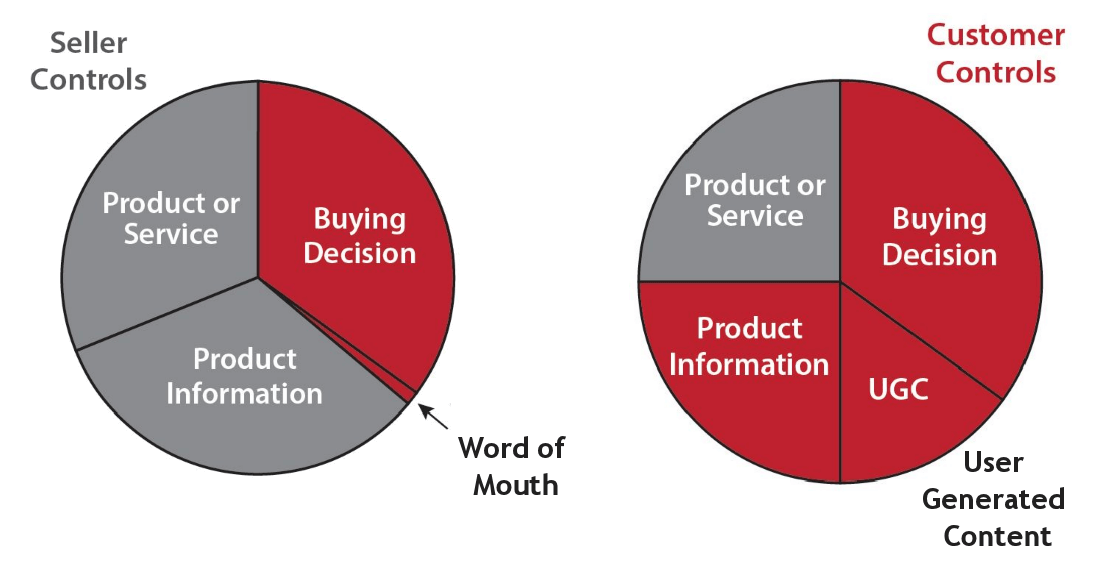
Image Source: The Age of the Customer, page 26
Blasingame further explains, “Compared to the historical timeline and pace of marketplace evolution, the shift to the Age of the Customer is happening at light speed. Nevertheless, since the Age of the Seller was the original standard by which markets were born and flourished for thousands of years, complete conversion will take time. Consequently, the two Ages now exist as parallel universes and will do so until the old Age finally succumbs to the new one.”
Figure 2. Parallel Universes.
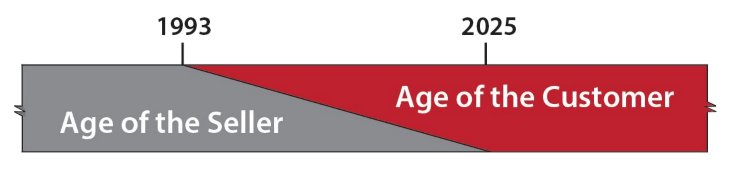
Image Source: The Age of the Customer, page 29
This means that in less than 10 years, businesses will either have converted their business plans to account for doing business in the age of more customer control, or they will continue to operate using outdated thinking until the diminishing supply of old-style customers is depleted, and they are left with no business prospects.
Get Blasingame’s book to understand fully why security industry business model disruptions are not solely caused by disruptive technologies (as is commonly discussed), but are also due to the larger and more powerful force that is creating a permanent shift in the way customers are willing and able to do business.
Mega-Risk No. 1: Sellers Can’t Hide Mistakes
Seller mistakes and deficiencies are amplified by 21st century customer online communities. This is a more significant and growing risk than most sellers realize. As Blasingame explains in detail in Chapter 6, “The Influencers”, and as I am oversimplifying here, the growing trend is for prospects and customers to go first to independent online sources of information about a seller and the seller’s products, and then use that information to evaluate the seller and the seller’s own information. A customer can self-qualify as a prospect for a seller’s offering, without any direct contact with seller, and then can disqualify the seller also without any direct contact with the seller, and quickly move on to the seller’s competition.
The negative effects of making mistakes in seller verbal and written information are amplified as described above. This is happening in all industries, including the security industry. When it comes to cloud computing and cloud services, there is a large universe of cloud-savvy IT and business personnel who are very knowledgeable about cloud computing, cloud services and cloud-based offerings. It only takes one individual who is more technically savvy than the seller’s own marketing, sales or technical personnel are, to identify and shine a spotlight on a seller’s disqualifying mistakes. The same is true for any negative experience that a customer has with a seller.
This is a particularly important consideration for security industry companies who are offering, or planning to offer, cloud services. End users have communities where security-related cloud services are being discussed and evaluated. Security integrators also have such communities, including IPVM.com.
There have always been risks relating to vendor mistakes and deficiencies, but Mega-Risk No. 1 amplified them to such a degree that Mega-Risk No. 2 is a serious consideration.
Mega-Risk No. 2: Inadequate Understandings of Advancing Technologies
For example, let’s look at how an inadequate understanding of cloud computing security – and the cloud itself – affects the security industry’s reputation for being cloud-savvy—or not so savvy. Security is one of Microsoft’s key selling points for its Azure brand of cloud services. Microsoft provides plenty of information about the security features of Azure, including an overview titled, “10 Things to know about Azure Security” (http://bit.ly/azure-security-10-things). When you read this overview, it is plain to see that Microsoft provides security for its own Infrastructure-as-a-Service and Platform-as-a-Service offerings, not for the cloud-service provider’s hosted application. The overview’s initial paragraph says, “Under the hood, the Microsoft Azure infrastructure implements a number of technologies and processes to safeguard the environment. This page covers how Microsoft’s Global Foundation Services runs the infrastructure and the security measures they implement.”
Another article, “Secure an app in Azure App Service” (http://bit.ly/azure-app-security), states, “While Azure is responsible for securing the infrastructure and platform that your application runs on, it is your responsibility to secure your application itself. In other words, you need to develop, deploy, and manage your application code and content in a secure way. Without this, your application code or content can still be vulnerable to threats.” (I added the bold emphasis in that quotation.) It is the software provider’s job to design application security into cloud Software-as-a-Service (SaaS) offerings — it is not the job of Azure or any other cloud infrastructure provider. This is the source of Mega-Risk No. 2: Inadequate understanding of cloud computing security.
Recently, several security industry providers of cloud-based offerings have proudly told me that they had moved their offering to Microsoft Azure, because of Azure’s high security. When I asked them to provide me with an application security architecture diagram for their Software-as-a-Service offering, they had no idea what I was talking about. The common response: “It is the Microsoft Azure cloud architecture.”
This could not have been a more incorrect response. The cloud infrastructure platform’s architecture (such as Azure or similar services) is definitely not the same thing as the security architecture for a hosted Software-as-a-Service application. Software application security is completely the SaaS vendor’s responsibility, not that of the cloud platform provider.
Investors, business owners, product managers and resellers all need to have a very clear understanding of this. I know of several security industry companies with SaaS offerings whose owners and investors will not allow them to spend money on documenting their security – or fixing it if need be – until a specific sales or profitability target is reached. If the company cannot provide documentation on the security of its SaaS offering, how can a customer’s technology evaluator approve the use of that offering?
A lack of security documentation puts a lid on sales, especially as prospective customers disqualify the vendor and spread the word. Any owner or investor should be able to prove to a cloud-knowledgeable evaluator that the security of its cloud-based application is sound and based on good practices. As mentioned in the previous article in this series, the Cloud Security Alliance (CSA) is defining and raising awareness of best practices for a secure cloud computing environment. The same companies I recently talked to, who had misunderstandings about the scope of Azure security, also had no knowledge of the Cloud Security Alliance – and neither did their software developers.
Heaven forbid that someone from a prospective customer’s IT department should start asking questions to the folks that I previously talked to. It’s okay to not know an answer; it’s definitely not okay to give a wrong one.
Get Ready for Advanced Show Floor Questions
Get the three Key Questions that will help you avoid the most critical show floor question risks. And if you like, get assistance with a specific list of Top 20 Most Challenging Show Floor Questions.

